Automations use cases (Beta)
The Automations feature is currently in Beta.
Notifying a team to complete a survey for a new project
Send out email notifications to project members when a new project is created so that they know to fill out the project survey. The email can contain a link to the survey by using a Project Placeholder.
Send an email notification when a new project is created
To create a new Automation that sends an email notification to project members when a new Project is created.
-
User require these permissions:
-
Manage → Global Roles → Automations → Create and edit automations
-
-
From the gear icon menu, select Automations.
-
Click the plus button for a New Automation.
-
Enter a unique name for this Automation.
-
Select "Project Created" from the Event dropdown.
-
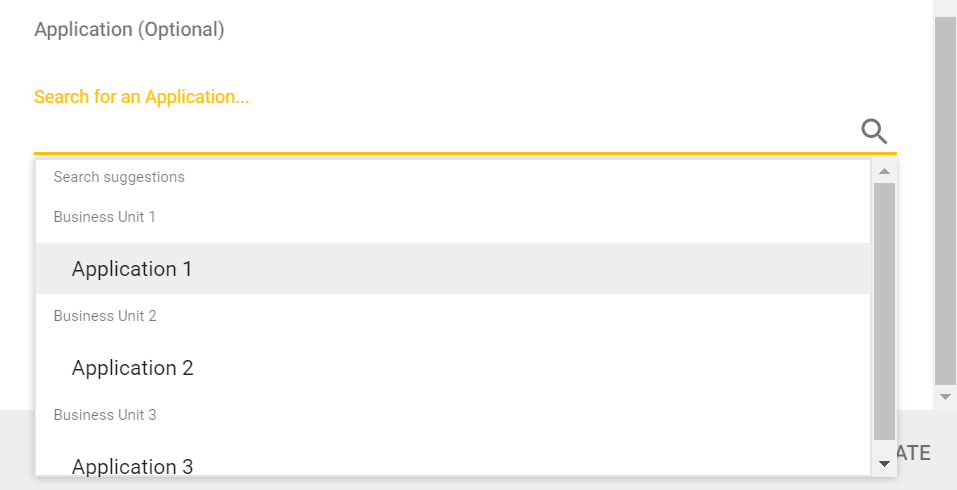
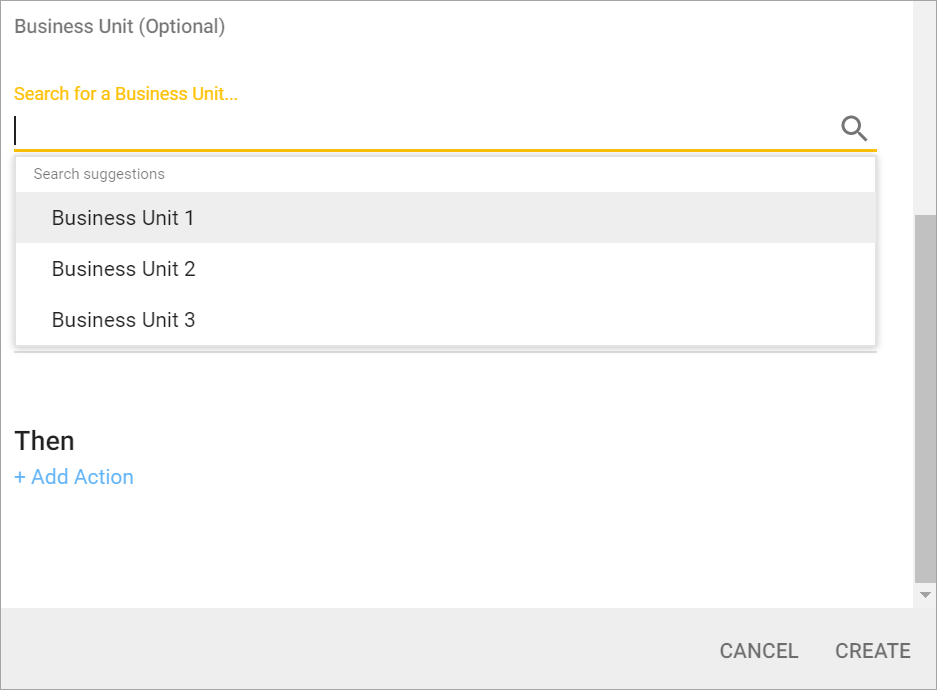
Leave Business Unit and Application blank so that the Event matches a new Project created in any Business Unit or Application.

-
Click on "+Add Action" and select Send email notification.
-
Fill out the email fields. All fields accept Project Placeholders.
-
Enter ${project_members} in Recipients. This will email all project members. You can alternatively list specific email addresses separated by commas. All emails entered must belong to registered SD Elements users.
-
Enter your email Subject. e.g. "New project ${project_name} has been created"
-
Enter your message in Message. e.g. "A new project called ${project_name} has been created in ${application_name}. Please complete the survey at this link ${survey_url}
-
A new project named "My Points" is created. An email with the subject "New project My Points has been created" is sent to members of this new project. The body of the email message is "A new project named My Points has been created in Mobile. Please complete the survey at this link http://sdelements.example.com/bunits/financial-unit/mobile-app/my-points/tasks/survey/questions/"
Keeping the project updated with security testing activities
Mark a security testing Countermeasure as complete when a verification scan has been run on the software. Here is an example of the criteria to enter:
{
"vulnerability_report": {
"SAST": {}
}
}
If you want to update the Countermeasure only with SAST scans that have no critical or high severity findings, use this:
{
"vulnerability_report": {
"SAST": {
"critical": 0,
"high": 0
}
}
}
For a scanning tool that performs both SAST and DAST scans, and you want no findings in either category, use this:
{
"vulnerability_report": {
"SAST": {
"critical": 0,
"high": 0,
"med": 0,
"low": 0,
"info": 0,
"unknown": 0
},
"DAST": {
"critical": 0,
"high": 0,
"med": 0,
"low": 0,
"info": 0,
"unknown": 0
}
}
}
A match occurs only if the scanner returns both types. If your tool does only SAST scans, you should specify only SAST finding limits.
Regularly perform security activities
To ensure that the project is getting SAST scans run on the software every 4 weeks, configure a Verification tool ran has not occurred over a time period event with the following criteria:
{
"category": "SAST"
}
and a Threshold value of 28 days. The Threshold value is the field labeled with "of" in the UI.
To ensure that the project is getting SAST scans run on the software every 4 weeks, and that there are no critical findings each time, configure a Verification tool ran has not occurred over a time period event with the following criteria:
{
"category": "SAST",
"severity_counts": {
"critical": 0
}
}
and a Threshold value of 28 days. The Threshold value is the field labeled with "of" in the UI.
If no events matching the criteria are found to have occurred within the Threshold, then the configured action is performed.
For both of the above examples, configure an Action to update Countermeasure "T1368: Perform security testing using SAST tools" to an incomplete status. Custom Countermeasure statuses are supported. The project, in this case, will not be compliant and should not be released.
Mark a Countermeasure as complete when a SAST scan tool is run
To create a new Automation that marks the project Countermeasure "T1368: Perform security testing using SAST tools" as "Complete" when the event occurs.
-
User require these permissions:
-
Manage → Global Roles → Automations → Create and edit automations
-
-
From the gear icon menu, select Automations.
-
Click the plus button for a New Automation.
-
Enter a unique name for this Automation.
-
Select "Verification tool ran" from the Event dropdown.
-
This event can have complex criteria, so the beta version accepts the criteria in JSON format.
{ "vulnerability_report": { "SAST": {} } } -
Keep the default selection of "has occurred".
-
Click on "+Add Action" and select Change countermeasure status
-
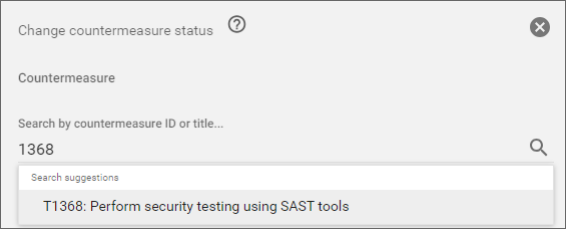
Select "T1368" in the Countermeasure field.
-
Enter "Complete" in the Status field.
When a SAST scan tool is run, and the findings are imported into an SD Elements project via integrations, the event and results will be detected by the automation you just created. The automation will then change the project’s Countermeasure T1368 to Complete.
Mark a Countermeasure as incomplete when a verification scan has not been run for 30 days
To create a new Automation that marks the project Countermeasure "T1368: Perform security testing using SAST tools" as 'Incomplete' when the event has not occurred within 30 days. In other words, the last SAST scan tool results imported are more than 30 days old.
-
User require these permissions:
-
Manage → Global Roles → Automations → Create and edit automations
-
-
From the gear icon menu, select Automations.
-
Click the plus button for a New Automation.
-
Enter a unique name for this Automation.
-
Select "Verification tool ran" from the Event dropdown.
-
This event can have complex criteria, so the beta version accepts the criteria in JSON format.
{ "category": "SAST", } -
Select "has not occurred over a time period".
-
Set the "of" field to 30 days. This field represents the threshold.
-
Click on "+Add Action" and select Change countermeasure status
-
Enter "T1368" in the Countermeasure field.

-
Enter "Incomplete" in the Status field.
When the Threshold monitor runs at its next scheduled time, it looks into past scan tool imports for each project, and finds the latest scan. Only scans that were imported after the Automation feature was enabled will be included in the monitoring.
The Threshold monitor will check if the latest scan occurred within the configured threshold. The latest scan for one was 45 days ago, which is beyond the configured threshold value. The threshold has been crossed, so Countermeasure T1368 in this project will be set to Incomplete. If the last scan were 30 days ago, or 5 days ago, then the configure action would not run.
The monitor continues through all the project, setting T1368 to Incomplete in each project with a latest scan date and time that crosses the threshold value. After all projects have been checked, the monitor stops until its next scheduled run.
| The date and time used to check against the Threshold is the scan date and time, not the import date and time. |
