sudo yum check-update
Ongoing tasks
- Check for newer system packages
- Update system packages
- Apply custom system configuration
- Use a trusted certificate to access SD Elements with a browser
- Trusting third party integration TLS/SSL certificates
- Verify a TLS/SSL certificate is trusted
- Examine logs
- Remove older application releases
- Open the application shell
- Confirm the version for the integration components
- Activate a different application release
- Turn on maintenance mode
- Turn off maintenance mode
- Reset the password of an application user
- Grant super user access to an application user
| As of SD Elements 2024.2, the container deployment is the only deployment model offered for self managed instances of SD Elements. See the Container Migration Guide for information on migrating your VM instance to a Kubernetes and the Container Deployment section for documentation on installing and maintaining an SD Elements container deployment. |
Certain tasks may repeat during the lifetime of the system. These tasks may be due to a need to troubleshoot an issue, support new integration systems, or perform maintenance.
Check for newer system packages
Retrieve a list of system packages that can be upgraded using the following steps:
-
Console or SSH access to the instance.
-
sde_adminuser credentials (included in thesdeandsde_admingroups). -
Outbound HTTPS access to
anvil.sdelements.com.
-
Access the SD Elements server as a user with superuser privileges.
-
Run the following command:
The process returns a list of all package updates.
Update system packages
Update system packages to their latest available version.
-
Console or SSH access to the instance.
-
sde_adminuser credentials (included in thesdeandsde_admingroups). -
Outbound HTTPS access to
anvil.sdelements.com.
-
Access the SD Elements server as a user with superuser privileges.
-
Run the following command:
sudo yum update
Confirm that the update should proceed by pressing the 'y' key. The process may take a few minutes. The system packages are then updated to the latest version.
Apply custom system configuration
System configuration is managed through /etc/sde/custom.yaml settings. Apply these settings
by following the steps below.
Configuration and customization changes performed without corresponding changes in custom.yaml can
and most likely will be overwritten unless explicitly excluded in the aforementioned custom.yaml file.
|
-
Console or SSH access to the instance.
-
sde_adminuser credentials (included in thesdeandsde_admingroups).
-
Access the SD Elements server console as a member of the
sde_admingroup. -
Update the file
/etc/sde/custom.yamlwith the desired changes. The list of supported options for the installed release can be found in/etc/sde/custom.yaml.exampleon the system or a generic list of options are listed in section System configuration options. -
Run:
sudo sde reprovision --offline-mode
The process may take a few minutes. The system will be reconfigured according to the custom.yaml file.
Use a trusted certificate to access SD Elements with a browser
An on-site deployment ships with a self-signed certificate. Change the SSL certificate to one that is trusted by clients to access web applications whose certificates are trusted by their browser.
-
SSH credentials for
sde_admin. -
TLS/SSL Certificate Authority (CA) certificate file in PEM format.
-
The certificate
.crtfile (includes the host certificate), and any intermediate or root certificates. -
The new private key file.
-
Upload the new private key to
/etc/pki/tls/private/. -
Upload the
.crtfile to/etc/pki/tls/certs/. -
Access the SD Elements server SSH console as
sde_admin. -
Edit
/etc/sde/custom.yamlto reference the new key and.crtfile so that the following lines are uncommented, and the files reference the new key and certificate, respectively:role::sdelements_server::ssl_key: '/etc/pki/tls/private/new_private_key.key' role::sdelements_server::ssl_cert: '/etc/pki/tls/certs/new_trusted_certificate.crt'
-
Run the following command:
sudo sde reprovision --offline-mode sudo sde nginx restart
You can now connect to SD Elements with a web browser to confirm that the certificate in use is correct.
Trusting third party integration TLS/SSL certificates
Follow the steps below to configure the system for a new TLS/SSL certificate.
-
sde_adminuser credentials (included in thesdeandsde_admingroups). -
TLS/SSL Certificate Authority (CA) certificate file in PEM format.
-
Create a folder called
/etc/sde/custom_ca_certs:mkdir /etc/sde/custom_ca_certs.
-
Set appropriate permissions:
sudo chmod 755 /etc/sde/custom_ca_certs
-
Place any custom certificate files in the new folder and ensure these have the appropriate permissions, where
certificate.crtis the certificate file:sudo chmod 644 /etc/sde/custom_ca_certs/certificate.crt
-
Ensure that the option
role::server::custom_ca_certsin/etc/sde/custom.yamlis active and configured for the location of the certificate, if that location is not/etc/sde/custom_ca_certs. -
Run the following commands:
sudo sde reprovision --offline-mode sudo sde supervisor restart all
The system trust store will be updated to include the certificate. All SD Elements Integrations will now include the new Certificate Authority when validating TLS and SSL secured connections.
Verify a TLS/SSL certificate is trusted
Check that a TLS/SSL certificate is trusted using the steps below.
-
Console or SSH access to the instance.
-
SSH credentials for a valid user on the system.
-
Fully qualified hostname and port (usually 443) for the target server.
-
Access the SD Elements server SSH console.
-
Verify the system’s configuration by checking that it has been successfully configured to trust a remote certificate signed by Custom Certificate Authority. Use the steps below:
-
If you have direct access to hostname:port, run:
openssl s_client -connect hostname:port
-
If you rely on a proxy to access the hostname from the SD Elements Server, run:
curl https://hostname:port/
-
-
Verify the application’s configuration by checking that it is set up correctly for a new certificate. Use the steps below:
-
Log in to the SD Elements web application.
-
Open an Issue Tracker connector configured for hostname:port and click "Test Connection".
-
The new certificate is now verified.
Examine logs
To diagnose application issues follow the steps below to access the application logs:
-
Console or SSH access to the instance.
-
sde_adminuser credentials (included in thesdeandsde_admingroups).
-
Access the SD Elements server SSH console.
-
Change to the logs directory:
cd /docs/sde/log/
-
Examine the log files
-
Use the tail command to watch logs as they occur:
tail -f /docs/sde/log/sdlc.log
-
Search for certain TEXT in logs by using grep:
grep -i TEXT /docs/sde/log/apache_error_sde_VERSION.log
-
Refer to Log files for details on which log file to examine.
When sharing details with SD Elements Support, use tail -100 logfile to collect context about an unexpected event. This command returns the last 100 lines from logfile.
|
Remove older application releases
The system retains older application releases and their data after an upgrade. To keep only recent releases and delete the others follow the steps below.
-
SSH credentials for
sde_admin. -
The number of recent releases to keep.
-
Access the SD Elements server SSH console as
sde_admin. -
To keep the two most recent releases, for example, run:
sudo sde manage_releases keep 2
All but the two most recent releases are kept on the server. Older releases and their data are deleted.
Open the application shell
The application shell provides low-level access to the data elements and functionality using a custom script. Open the shell using the steps below.
-
SSH credentials for
sde_admin.
-
Access the SD Elements server SSH console as
sde_admin. -
On the command line, run
sde manage_django shell_plus. A Django shell opens with direct access to the application. -
Type the script into the console and press <enter> after each statement.
-
Push Ctrl+D or type
quit()to stop the shell.
All changes made in the shell are permanent.
Confirm the version for the integration components
Follow the steps below to output the version of the integration components
sdetools.
-
SSH credentials for
sde_admin.
-
Access the SD Elements server SSH console as
sde_admin. -
On the command line, run the following command:
sde pip live freeze | grep sdetools
The version of sdetools is printed to the console.
Activate a different application release
Prior releases are kept on the server after an upgrade. During testing, it may need to revert to an earlier release. To switch to a different application release of SD Elements, follow the steps below.
-
Console or SSH access to the instance.
-
sde_adminuser credentials (included in thesdeandsde_admingroups). -
The fully qualified application release name. For example, "4.12.13".
-
The application release is installed on the server.
-
Access the SD Elements server as a user with superuser privileges.
-
On the command line, run the following command:
sudo sde activate_release --release 4.12.13
The current release of SD Elements and its data are left intact on the server. The active release of SD Elements is changed to the selected version and the server is reprovisioned. The application data contains the information stored when the selected release was last used.
Turn on maintenance mode
Pause the application and inform users that it is temporarily unavailable with the steps below.
-
SSH credentials for
sde_admin.
-
Access the SD Elements server SSH console as
sde_admin. -
On the command line, run the following command:
sde maintenance on
Users are greeted with a web page stating the application is offline. All HTTP responses are sent with error 503.
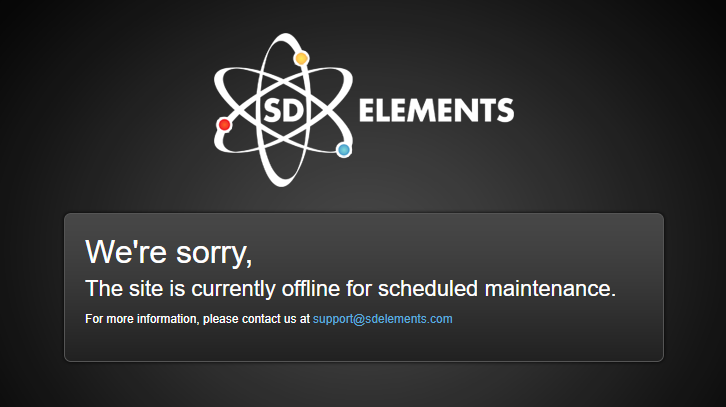
Turn off maintenance mode
Resume the application for users using the steps below.
-
SSH credentials for
sde_admin.
-
Access the SD Elements server SSH console as
sde_admin. -
On the command line, run the following command:
sde maintenance off
The application is back to normal operation.
Reset the password of an application user
To reset the password of a web application user, follow the steps below.
-
SSH credentials for
sde_adminor sudo access. -
User email address. For example: user@example.com
-
Access the SD Elements server SSH console as
sde_admin. -
On the command line, run the following command:
sde manage_django changepassword user@example.com
-
Enter the new password when prompted.
The password is reset.
Grant super user access to an application user
Access to SD Elements application data and settings is generally controlled by the in-app Global and Project roles, as well as group and business unit membership. However, there are certain capabilities that are reserved to a special class of user, a Superuser.
By default every organization has a single Superuser. The Superuser has full application access, including the ability to modify the following items:
-
Countermeasure Statuses
-
Domain Settings
-
Single Sign-On settings
-
Custom Application and Project Attributes
The default super user is "support@sdelements.com". To grant superuser access to an application user, such as "admin@example.com", follow the steps below:
-
SSH credentials for
sde_adminor sudo access.
-
Type the following in your shell and replace the example email address with the one you wish to affect in your instance:
from users.models import User u = User.objects.get(username="admin@example.com") u.is_superuser = True u.save() quit()
The user "admin@example.com" is given superuser access. Additional menu options and capabilities are now available for the user.
To disable superuser access change u.is_superuser = True to
u.is_superuser = False in the above script.
|
